무엇을 찾고 있습니까?
Device Vulnerability Analysis
Bolster your device security at every stage of development.
Every part of your device, from chip to end product, is a target for cyberattacks. That’s why security needs to be built in from the start. Keysight can help. We provide the latest advancements in testing to secure your semiconductor, embedded system, or IoT device at every stage of development. Our team of trusted security experts is ready to help you speed up certifications and compliance, strengthen your security practices, and stay ahead of the latest threats.

Riscure is Now Part of Keysight
Riscure, a leader in device security, is now part of Keysight. Riscure is a pioneer in fault injection testing and side channel analysis, bringing unparalleled expertise to Keysight's security portfolio. As one company, we can help you safeguard your devices at every stage of development.
Our expanded team of security experts is ready to provide comprehensive security evaluations, guidance on industry certifications, and tailored training programs to equip your developers with the latest security best practices.
DS1050A Next-Generation Embedded Security Testbench
The DS1050A Next-Generation Embedded Security Testbench is a cutting-edge PXI-based solution for Side Channel Analysis (SCA) and Fault Injection (FI). Its integrated design accelerates chip and device security testing, offering high-speed performance, flexible configurations, and robust reliability.
Your Complete Security Partner

Security Certifications
We'll guide you through the certification process to ensure your device meets industry standards like EMVCo, MovieLabs, Common Criteria, and more.

Security Evaluations
Our security experts will meticulously assess the security of your devices and components, helping identify and mitigate vulnerabilities.

Security Trainings
Equip your team to proactively address security challenges and safeguard your organization with our comprehensive training programs.
Fault Injection Testing
Fault injection testing is crucial for safeguarding embedded systems and smart cards. The Keysight Inspector FJ2 Fault Injection System simulates a wide range of fault conditions so you can proactively assess your devices' resilience and protect against vulnerabilities.
- Induce faults in cryptographic algorithms, authentication checks, and other critical chip operations.
- Perform precise laser-based fault injection to uncover vulnerabilities.
- Tailor the system to meet your research needs.

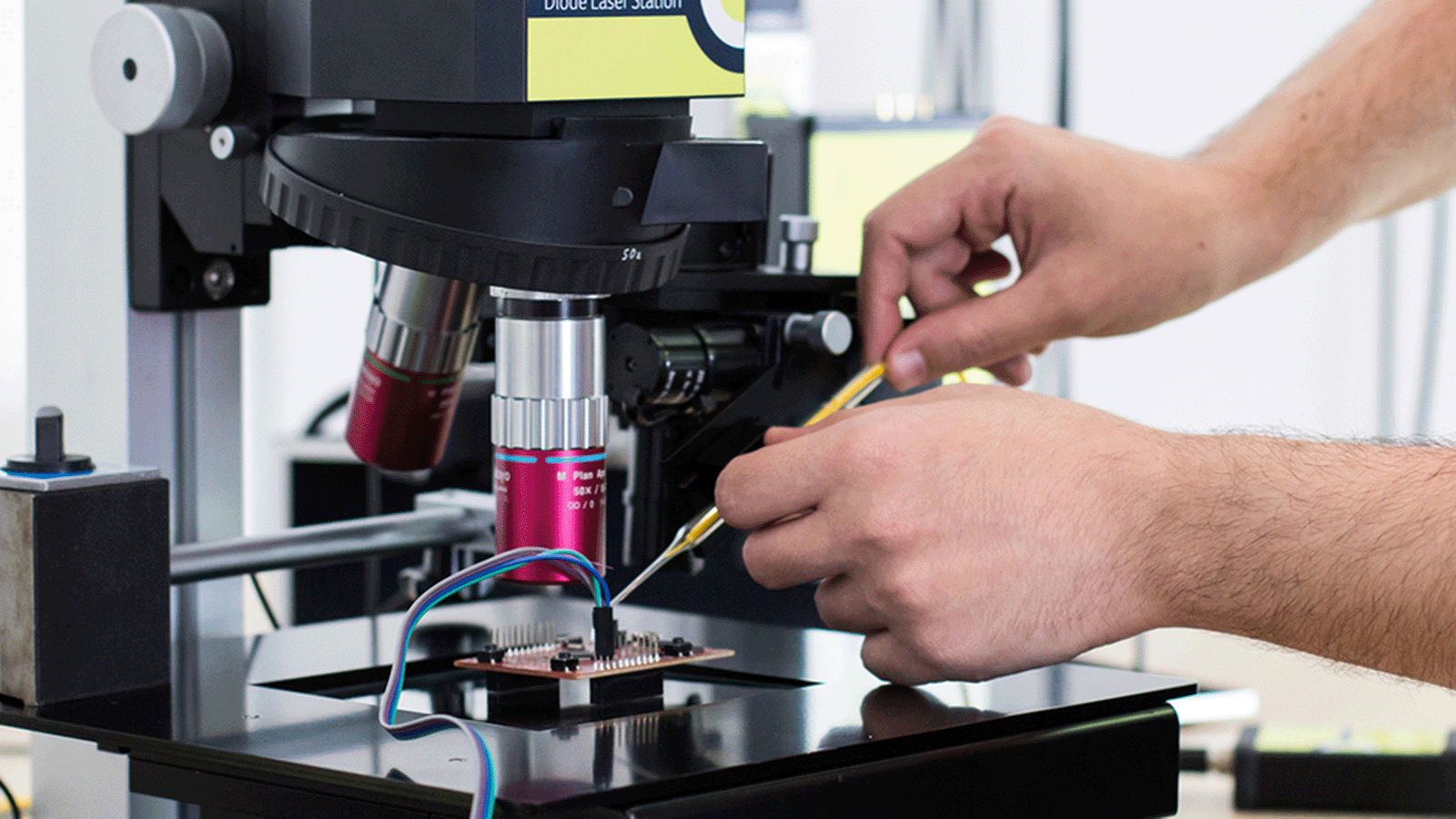
Side Channel Analysis
Side channel analysis identifies hidden vulnerabilities in embedded devices, chips, and smart cards. The Keysight Inspector SC4 Side Channel Analysis solution analyzes physical characteristics like power consumption or electromagnetic emissions to help you uncover sensitive information that traditional security measures may miss.
- One solution for power, electromagnetic, and contactless side channel testing.
- Fast analysis and processing using application-specific custom measuring hardware.
- Highly configurable cryptanalysis modules supporting first-order and high-order attacks on all major algorithm.
Design and Test Software for Device Security
Pre-Silicon Side Channel Analysis
Keysight Inspector SC2 Pre-Silicon Side Channel Analysis helps you find side channel leakage and fault injection vulnerabilities in your designs pre-silicon — not post-silicon — and automatically identify the root cause.
- Leakage analysis: Find leakage that an attacker can exploit and detect the parts of the design that contribute to it.
- Root cause analysis: Point to gates on a physical level and translate to the RTL design to prevent security vulnerabilities.

Fault Injection Software
Keysight FJ2 Fault Injection System software helps you test whether you can extract a key by inducing faults in a chip’s cryptographic operations, bypass a check such as an authentication or a life cycle state, or change the program flow on a chip.
- Crypto: Perform side channel and fault injection security testing on a chip’s cryptographic functions
- Non-crypto: Introduce faults and identify security threats during chip development and design.

Side Channel Analysis Software
Keysight Inspector SC4 Side Channel Analysis software supports data acquisition and advanced cryptanalysis while testing embedded devices, chips, and smart cards. Our premium software extension accelerates side-channel analysis with deep learning and automated workflows.

