What are you looking for?
Bypass Switches
Failsafe devices to ensure uptime and high availability of monitoring and security deployments

Discover Keysight Network Bypass Switches
- Pre-configured heartbeats: The only bypass to work with security tools through a single click, reducing setup times and eliminating potential errors during deployment.
- Redundant or serial active tool support: Deploy multiple tools inline with a single bypass; the bypass supports active-standby and active-active network/security architectures.
- High-density ports: iBypass VHD has the highest-density ports of any Bypass switch. Can protect up to 12 network links or 12 security devices.
- Central management support: Ixia Fabric Controller Centralized Manager, the industry’s only centralized bypass management tool, simplifies and speeds configuration and management of tens to hundreds of devices.
- Market-leading GUI: Easy-to-use interfaces support rapid deployment of complex topologies that are not possible with other vendors' bypass switches.
- Multiple solutions: Keysight offers external bypass switches from 1G copper to 100G fiber — enabling complete independence from tool or packet broker failure.
Select the Bypass Switch That's Right for You
What Is a Bypass Switch?
Bypass switches are network hardware devices that act as failsafe mechanisms for inline network devices — meaning they're directly within the path of incoming network traffic. In the case of maintenance, service disruptions, or network outages, bypass switches automatically redirect traffic to maintain the network's core functionality. In addition, bypass switches can also mirror network traffic — sending packets directly to monitoring tools or to network packet brokers for de-duplication and distribution.
Bypass Switch Features
Protect Your Network From Interruption, An Inline Lifeline For Growing Networks
Inline tool risk is a problem. Networks face a continuously evolving barrage of security threats. Directly deploying inline security tools can create a line of defense, but these tools can also result in single points of failure. Even a potent mix of security and analytics tools can lead to risks as regular rebooting, maintenance, and upgrades increase the chances of costly network outages.
And in the event an inline tool becomes unavailable, it can completely bring down the network link, significantly compromising network uptime and disrupting business continuity.
Bypass Network Outages With Inline Protection
Our bypass switches provide failsafe, inline protection for networks of any size. These switches safeguard a network with automated failover protection, preventing temporary tool outages from escalating into costly network outages.
Deploying bypass switches between inline network devices and security tools provides a reliable separation point between the network and security layers.
The result: allowing your network and security tools to support and protect your business — without the risk of network interruptions. Better yet, these bypass switches allow multiple security tools to process traffic from a single network link and offer many unique capabilities like pre-configured heartbeats, centralized management, and support for redundant or serial active tools using a single bypass.
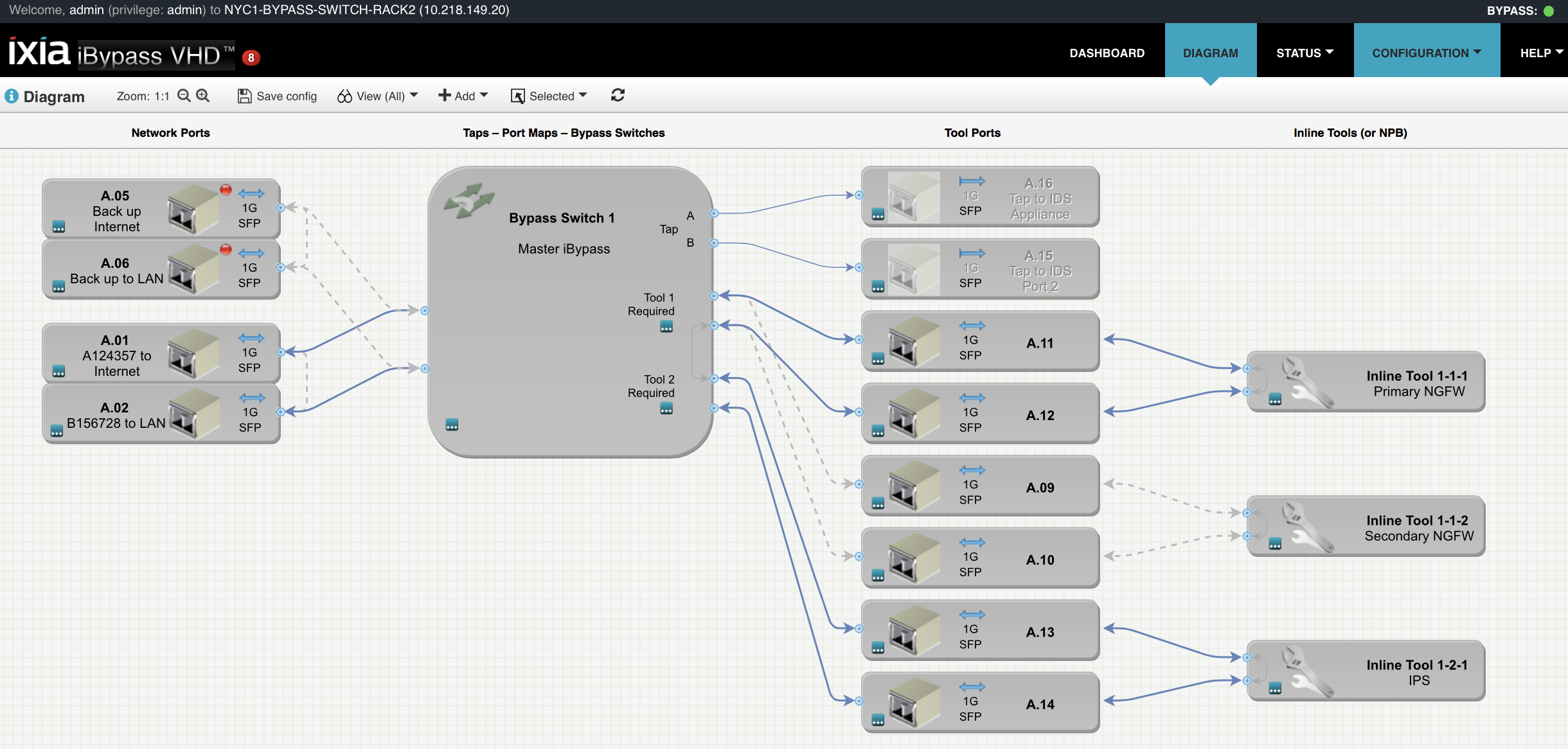
Example of a HA configuration for the iBypass VHD
The Broadest Array of External Bypass Switches
Keysight offers a range of five different Bypass Switches which are suitable for a range of different deployment scenarios. We are leaders in supporting "High Availability" (HA) capabilities that allow multiple tools to be deployed either in ACTIVE-ACTIVE (serial) or ACTIVE-STANDBY deployments. Our leading web based User Interface allows complex HA deployments to be configured quickly without the errors that less sophisticated interfaces can easily result in.
Our Bypass Switches are a perfect complement to our "inline" emulation tools such as the Network Emulator II. The Keysight Bypass Switch enables the Network Emulator II to be deployed in mission critical applications such as latency equalization within financial trading networks.

Summary of Features
- Independent Architecture
- Preset Security Tool Heartbeats
- Heartbeats Editable in the UI
- Easy-to-Use GUI
- Central Management
- Bypass Switch Density (per 1U): up to 12
- Redundant Tool Support
- Media Conversion
- Tap, Aggregate, Regenerate
- Form Factor: 1U
Protect Your Investment
Featured Resources
Bypass Switches: Frequently Asked Questions
Bypass switches offer failsafe protection for inline network monitoring tools and flexibility for network architects and operations teams. Since bypass switches deploy directly in the line of incoming network traffic, it's easy to reroute network packets away from offline tools — minimizing the impact of device outages, maintenance, and downtime.
Network bypass switches come in two different form factors: internal and external. Internal bypass switches are integrated into other network appliances, such as switches or network packet brokers. While their integrated functionality offers convenience, it comes at the cost of reduced control and flexibility.
In contrast to an integrated internal bypass switch, external bypass switches are separate devices that deploy on the network independently. Because these devices aren't linked to network appliances such as switches or network packet brokers, external bypass switches provide more control to network architects and operations teams.
Want help or have questions?








