What are you looking for?
SecureStack Software Suite
Optimized handling for secure traffic

Visibility is Security
Keysight allows organizations to shed the burden of many appliances by offering SecureStack capabilities on its visibility platforms — network packet brokers. Organizations know that security is visibility — you have to see the data to be able to secure it and prevent attacks.
With Keysight visibility you can decrypt and encrypt data and have the ability to mask data on your network without specialized appliances. Saving your organization dollars, helping IT and security teams, and all while better protecting your network.
Inline Decryption
Keysight's Inline Decryption capability enables organizations to see inside traffic that uses ephemeral key cryptography through its visibility platform. With our Inline Decryption, you can:
- Decrypt once and scale monitoring infrastructure. Offloading TLS decryption will optimize security and monitoring tool performance.
- Deploy inline, out-of-band (OOB), and simultaneous inline and OOB tool configurations for the ultimate flexibility.
- See into both outbound and inbound traffic to inspect downloads and detect server attacks.
- Achieve limitless visibility when used with our NetStack, PacketStack and AppStack capabilities.

Key Specifications
Inline Decryption
YES
Out-of-Band Decryption
YES
Data Masking Plus
YES
Offload TLS/SSL Decryption
YES
Want to see more specifications?
SecureStack Features

Inline Decryption
Decryption and Encryption with Ephemeral Key and TLS 1.3 Support
Encrypted traffic is a dual-edged sword, where the protection it provides can be manipulated by hackers to inject malware and other threats into a network. As most traffic becomes encrypted and with ephemeral key on its way to becoming the dominant technology, organizations need a way to retain the benefits of TLS 1.3 standards, while being able to inspect traffic for threats and malware to protect their networks and users.
Inline Decryption is available via separate high-performance application modules that are compatible with Vision ONE™ and Vision X™


Out-of-Band Decryption
Data encryption helps make information secure, but unfortunately, it can also be used by hackers to inject malware, viruses and other risky content into encrypted traffic and traverse your network without being detected. Get greater visibility by decrypting traffic to detect such malware, prevent data loss, monitor applications and more. We can help you offload the SSL/TLS decryption work and remove your network performance bottleneck.
- Get visibility to encrypted sessions without compromising security with role-based access controls and bidirectional decryption capability.
- Handle 10 million concurrent sessions with up to 8Gbps throughput within AppStack on the Vision ONE.
- Support encryption ciphers and key sizes: 3DES, RC4, AES, SHA1/521/384/256/224, MD5, ECC (Elliptic Curve), RSA and Diffie-Hellman Key Exchange.
- No impact on application identification and filtering performance.
- Can work simultaneously with NetFlow generation, data masking, PCAP, and application forwarding.


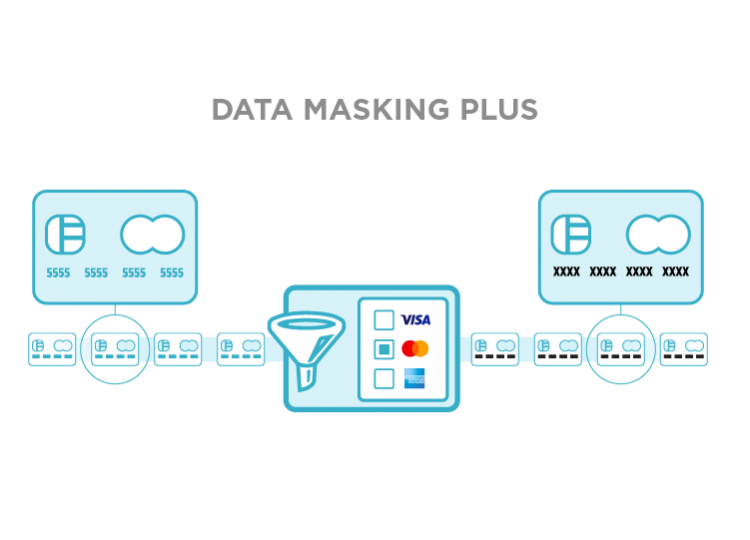
Data Masking Plus
With personally identifiable information traversing the network, security is key to keeping your consumers and your organization safe. Data Masking Plus helps you meet compliance regulations by securely masking sensitive data on your network such as credit card and social security numbers.
Data Masking Plus allows you to:
- Use pre-defined patterns to mask major credit cards, social security numbers, and email addresses.
- Use a configurable offset with any number of bytes to mask a specific place in a packet.
- Reduce false positives with built-in credit card number validation using the Luhn algorithm
- Achieve Payment Card Industry Data Security Standard (PCE-DSS), HIPAA, and other regulatory compliance.
Find Your Platform
Protect Your Investment
Featured Resources
Want help or have questions?












