What are you looking for?
Network Visibility
Better visibility into physical, virtual and software defined networks with network packet brokers, bypass switches, and network taps
2024 Frost & Sullivan New Product Innovation Award Winner

The Vision 400 Series Network Packet Brokers received the prestigious 2024 Global New Product Innovation Award from Frost & Sullivan. This innovative product line delivers unmatched performance, modularity, scalability, future-proof design, automation, intelligence, and an exceptional end-user experience.
Network Visibility For Hybrid Networks
The need for always-on networks is pervasive, and expectations are high when it comes to keeping them connected and secure. As technologies advance, edge computing, cloud environments, sophisticated security threats, bandwidth requirements, and compliance regulations make it challenging to extract actionable insight from your network.
Keysight can help. Customers rely on our network visibility solutions to deliver rich data about network traffic, applications, and users across any networking environment. These deep insights are what we call dynamic network intelligence. It helps you continuously innovate, meet aggressive service level agreements, and keep applications running smoothly and securely.
Find the Visibility Series That's Right for You

What Is Network Visibility?
Network visibility is monitoring all the traffic and data flowing across a network at any given time. Traditional network monitoring tools — such as security and network performance monitoring solutions — rely on data packets to perform their intended function. However, you can't secure what you can't see — and modern, distributed network topologies are rife with blind spots. Network visibility tools deploy across on-premise data centers, cloud-based hypervisors, and software-as-a-service applications to capture, aggregate, and filter network packets before sending them to downstream monitoring tools.
Find Your Visibility Platform
Dynamic network intelligence stack feature sets allow you to optimize your traffic analysis and security tool performance. Used with a network packet broker, virtual or cloud platform, stack feature sets allow you to modify, mold and transport traffic specific to tool needs. To learn more, click on a stack feature set below.
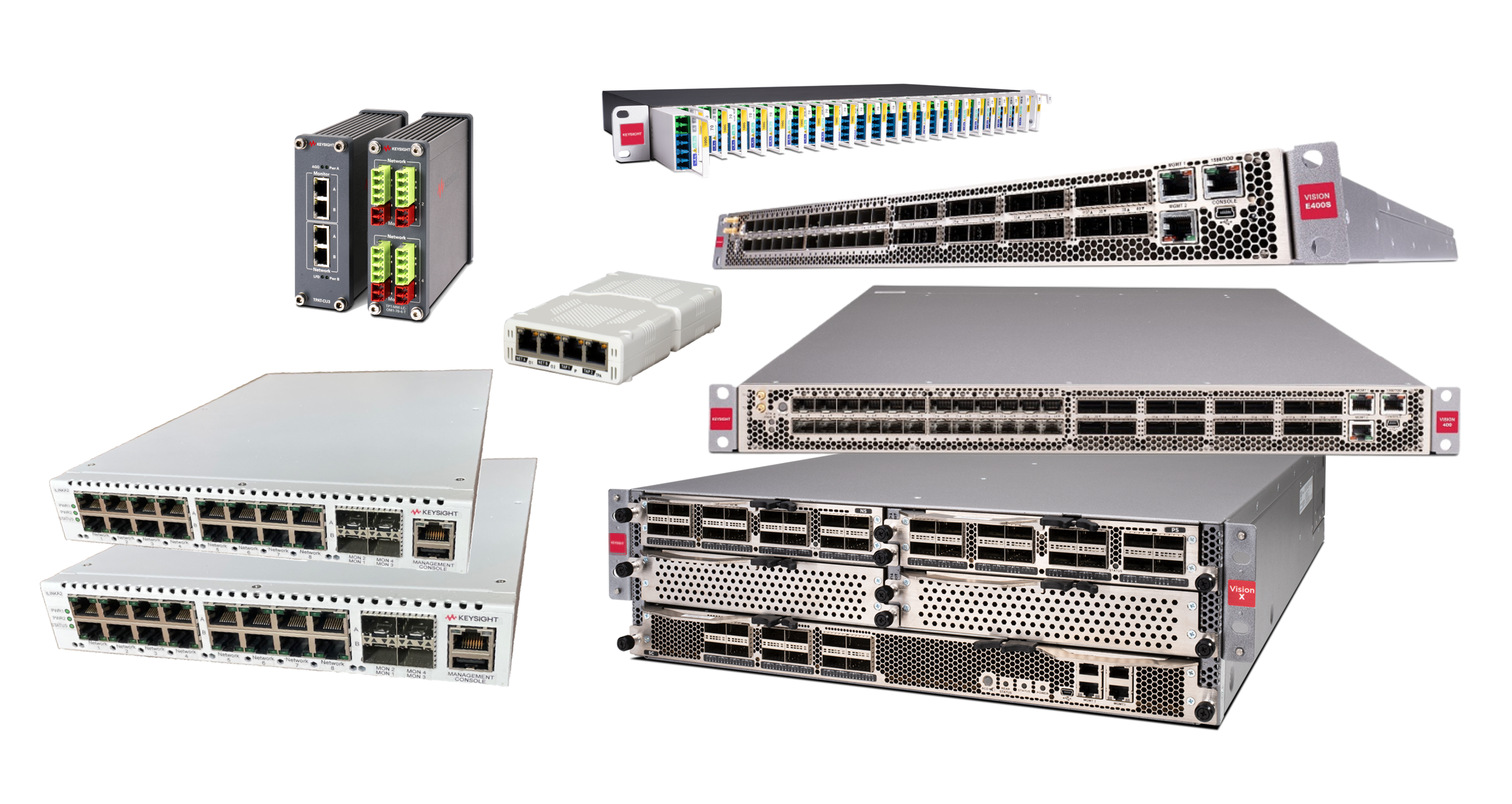
Network Visibility Portfolio
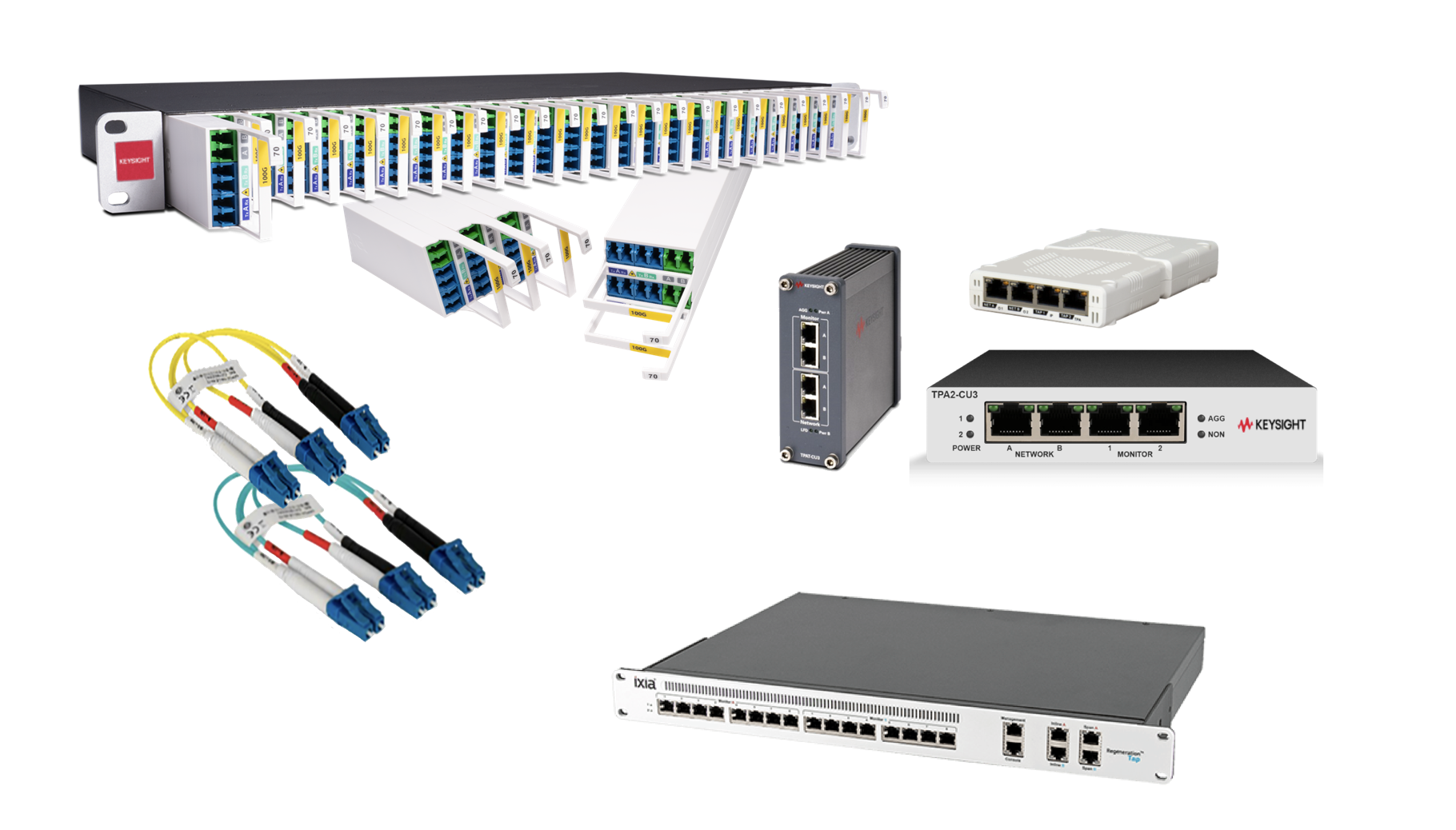
Access Network Data with Network Taps
Whether you're trying to pinpoint indicators of a security breach or tracking quality of service, your monitoring tools rely on packet data — sourced from all corners of your network. But how do you capture all that critical information — and make sure it gets sent to your tools efficiently? That's why Keysight offers a wide variety of network taps to capture network packets across the entirety of your network.
Aggregate and Filter Data with Network Packet Brokers
How do you ensure your network security and performance monitoring tools get all the data they need — and nothing they don't? You install a network packet broker (NPB) to aggregate, process, and filter packets before sending them along to your monitoring tools. Keysight NPBs offer advanced features like header stripping, de-duplication, and load balancing. Plus, unlike other NPBs, you can use all features at once. No compromises are required.
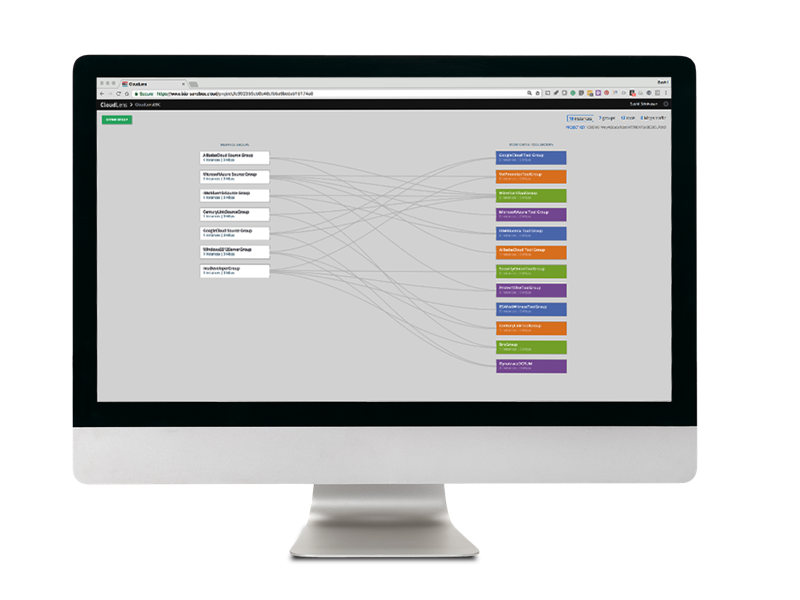
Cloud Visibility with CloudLens: Packet-Level Visibility For Public, Private, and Hybrid Cloud
Migrating mission-critical workloads to the cloud requires actionable intelligence for IT security and analytics tools — which are only as effective as the data they see. IT’s challenge is ensuring that the infrastructure delivers reliable, fast, and secure applications — especially as business changes force IT to gain greater insight and understanding of the network to maximize performance. Keysight CloudLens™ delivers end-to-end visibility and provides context-aware data processing across all cloud environments — public, private, and hybrid cloud — making applications stronger by providing a high level of network intelligence.
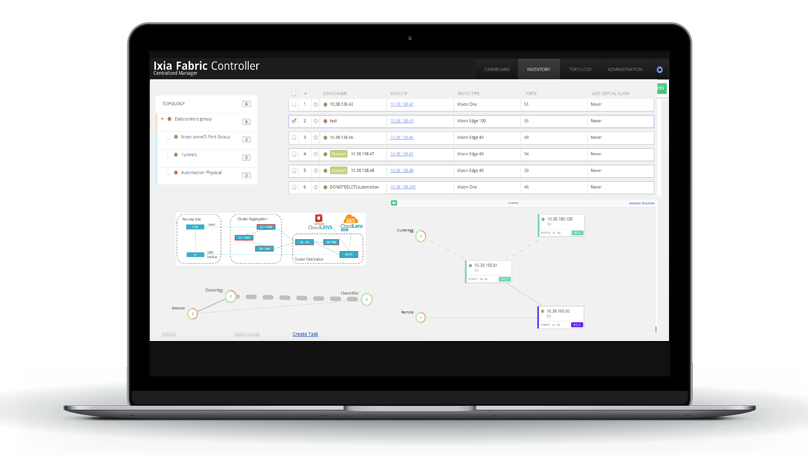
Visibility Management with Fabric Controller
Keysight offers an easy-to-use, intuitive click-and-drop NPB interface to allow operators to make connections from taps or SPAN ports to their connected tools. The configuration of filters is streamlined and straightforward, with minimal setup time and effort for large organizations and complicated networks. No professional services or expensive training is necessary — eliminating the need for time-consuming efforts using command line interfaces (CLI), web user interfaces (WebUI), or complex logic designs.
Fabric Controller is an SDN controller for visibility that allows multiple network packet brokers to work collectively within a single pane of glass. IFC extends a complete set of API controls and integrates with Cisco ACI, as well as other SDN architectures.
Network Visibility Technology Partners
Discover solutions for security, performance, and the cloud.

Featured Resources
Network Visibility: Frequently Asked Questions
Network visibility is crucial because it enables network operations teams to ensure that their monitoring tools always have a clear view of all network activity. Without network visibility tools capturing, aggregating, and filtering packets across physical and virtual network infrastructure, blind spots can hamper monitoring tools' effectiveness. Moreover, without the advanced filtering features of a network packet broker, tools can actually receive too much data — jeopardizing their efficiency and lifespan.
Network visibility tools can be separated into two categories: network packet capture and inline network infrastructure. Network packet capture tools include network taps, SPAN ports, and cloud visibility solutions. Inline network infrastructure appliances include bypass switches and network packet brokers.
Network visibility is a crucial aspect of network security. Many network security tools rely on network packets to monitor for potential breaches or identify indicators of compromise. However, your tools cannot secure what they cannot see — and blind spots can offer hiding places for cybercriminals. Modern distributed, hybrid networks require end-to-end visibility, spanning both physical data centers and virtualized network infrastructure.
Want help or have questions?