What are you looking for?
IoT Security Assessment
Latest News
Automated IoT Testing
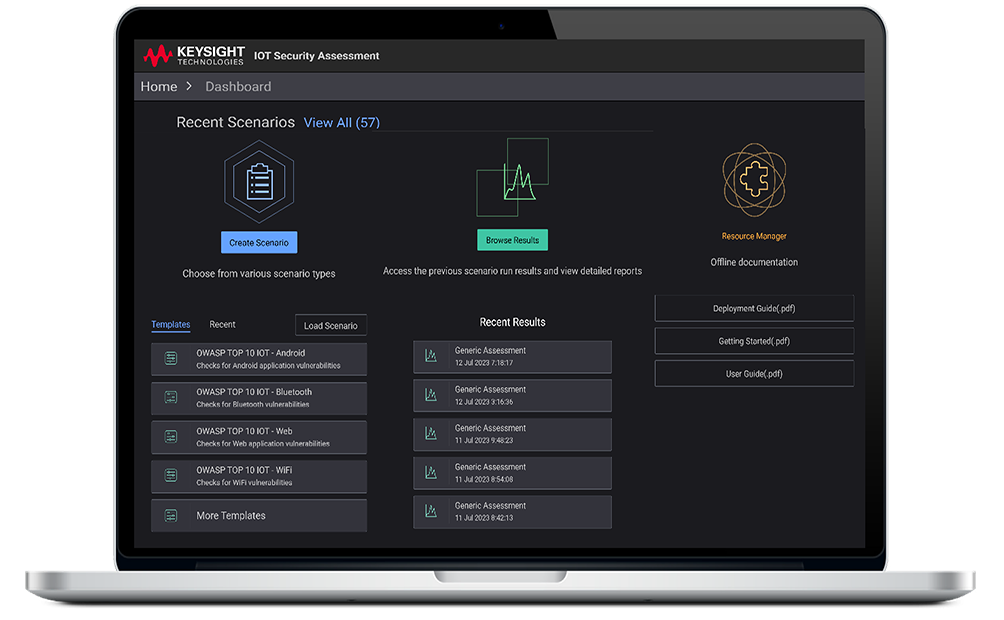
IoT Security Assessment
Unlike disparate solutions that require users to assemble and separately manage multiple tools, Keysight’s IoT Security Assessment combines traditional vulnerability assessment with industry leading protocol fuzzing as well as our new firmware analysis under an integrated user interface (UI) or REST API. This solution also includes comprehensive reporting on discovered security flaws.
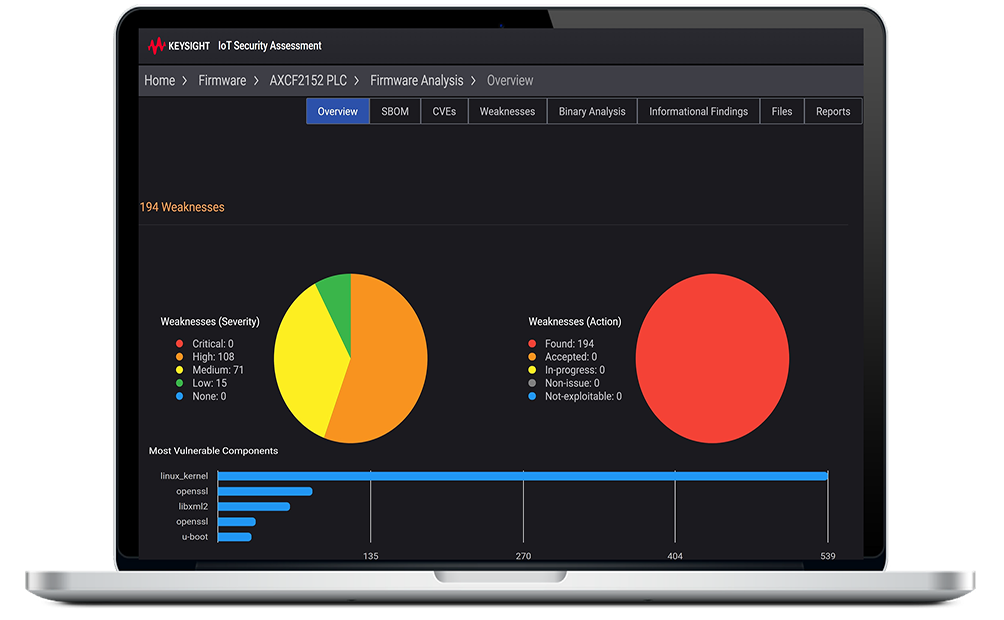
New Firmware Analysis Module
We can identify vulnerabilities directly within the device's operating code that includes everything from extracting the Software Bill of Materials (SBOM) to uncover associated vulnerabilities, detecting hard-coded credentials that pose unauthorized access risks, pinpointing configuration flaws, identifying weak or expired cryptographic keys and certificates, to finding vulnerable scripts and binary code.
Demo Video - IoT Security Test Plan
Why and how do you test IoT security? Discover how Keysight IoT Security Assessment can perform security tests for certification. Watch Scott Register, Keysight's VP of Security Solutions, navigate the tool's interface and run a sample test plan.
Automated IoT Security Testing
- Quickly find security flaws with intuitive UI
- Integrate security testing into CI/CD pipeline with complete REST API management
- Discover unknown network stack and chipset weaknesses with protocol fuzzing
- Harden security with vulnerability assessment
- Validate Wi-Fi, cellular, Ethernet, CAN bus, Bluetooth, and BLE connected devices
Trusted Across Multiple Industries
Automated cybersecurity validation for consumer IoT has huge potential for companies to make their compliance uniform and repeatable.
Discover how Keysight IoT Security Assessment can help manufacturers automate security tests for certification.
As IoMT’s role in healthcare grows, cybersecurity threats become all the more salient. When the stakes are this high, you can't leave anything to chance. That's why manufacturers and healthcare providers alike trust Keysight to make sure their devices can be trusted when it matters most.
In today’s vehicles, faster and better connectivity enables a host of new possibilities. Turning these ideas into reality depends on a host of connected components and millions of lines of software code. Proactive prevention starts with cybersecurity. With Keysight, you can find and fix potential weak spots before they can be exploited by hackers.

Operational technology (OT) and SCADA systems pose significant cybersecurity risks. Largely built on legacy technologies, these devices are easy targets for attackers, because they often haven't been tested against common exploits. Don't wait for attackers to find their way in. With the IoT Security Assessment, you can take matters into your own hands and harden critical devices against a full array of popular and emerging TTPs.

Cybersecurity is no longer just about protecting equipment and borders. Attackers aren't just looking at networks and data centers, they're taking aim at security gaps in aircraft, sensors, drones, and satellites. Assessing your security readiness has never been more important. That's why governments and contractors alike trust Keysight to fortify connected components, devices, and full-scale assemblies.

Featured Resources
Want help or have questions?











