What are you looking for?
BreakingPoint QuickTest
Turn-key performance and security testing
Already own this product? Visit Technical Support
Highlights
- Simplified user interface that enables execution of complex test cases in two to three clicks
- A self-stabilizing, goal-seeking algorithm to assess performance and security of a variety of infrastructures
- Continuously updated suites that ensure the assessments are based on the current state of the internet
- Pre-created problem-based test methodologies covering the top performance and security scenarios
- Expert post analysis of each test run that also provides actionable insights and recommendations based on the results
- Ability to use both BreakingPoint and BreakingPoint QuickTest from the same test platform
Validate Devices and Network Security With Real-World Applications and Threat Vectors.
Problem: Complexity of CyberSecurity Testing
A properly conducted cybersecurity assessment provides details about network or device performance while handling traffic of various complexities — from basic Layer 2–3 to web to complex application mixes with and without various threat vectors.
Similarly, a deep security-effectiveness assessment will need a combination of threat vectors and evasion techniques to accurately gauge an infrastructure’s capability to detect, allow, or block different types of attacks. This validation is critical to ensuring a high-performing and secure network.
However, many organizations do not perform these assessments on a regular basis because the tools capable of such testing are too complex, network configuration changes are too frequent, or they lack staff with the knowledge required to analyze test results.
Solution: Turn-Key Tests Designed to Accelerate Testing and Reduce Learning Curve
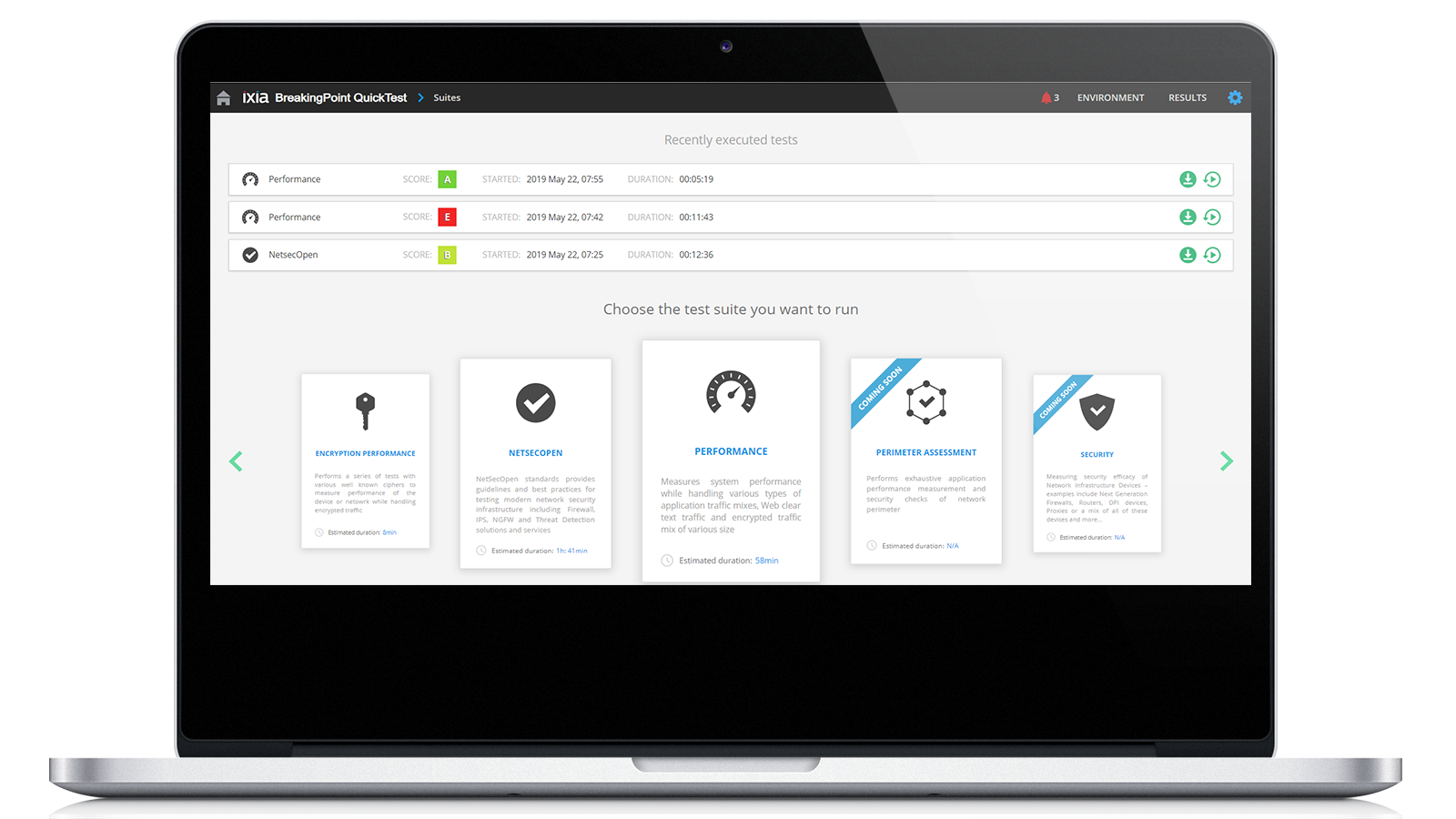
BreakingPoint QuickTest simplifies application performance and security-effectiveness assessments by providing individual test methodologies based on the type of test needed. Test suites included or planned near-term include encryption performance, NetSecOpen, system performance, perimeter assessment, and device security.
These easy-to-use test methodologies leverage the ongoing research from our global Application and Threat Intelligence (ATI) team and the many years of experience Keysight engineers have in testing various application and security devices and networks.
The test suites employ powerful stabilization and goal-seeking algorithms and expert analysis that ensure accurate assessment of a diverse set of devices and systems and deliver actionable insights after each test run.
BreakingPoint QuickTest delivers all the power of our industry-leading BreakingPoint, enabling organizations to optimize the speed of their cybersecurity testing without compromise.
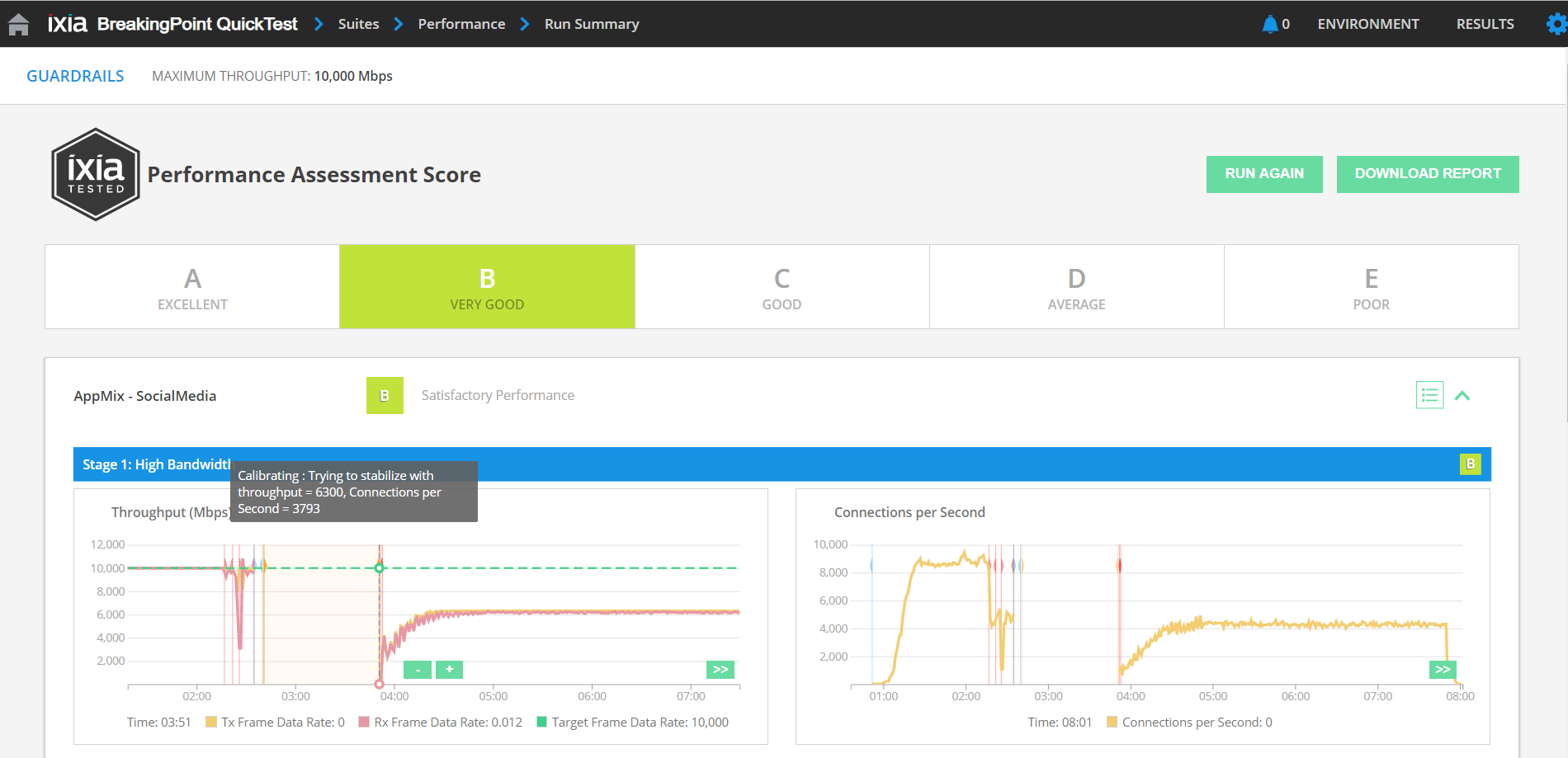
The BreakingPoint QuickTest stabilization/calibration algorithm handles a diverse setup of traffic conditions and finds the optimum performance/security results
Featured Resources
Related Products
Want help or have questions?