segmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6gsegmentation:funnel/bofu,keysight:product-lines/di,segmentation:campaign/Cellular,keysight:dtx/solutions/facets/industry/wireless-communications,segmentation:product-category/Cellular_Device_Network_Testing/Cellular_Device_Testing,segmentation:product-category/Cellular_Device_Network_Testing,segmentation:business-unit/CSG,keysight:dtx/solutions/facets/development-area/rf,keysight:dtx/solutions/facets/workflow-stage/functional-test,keysight:dtx/solutions/facets/industry/aerospace-and-defense,keysight:dtx/solutions/facets/design-and-test-product/wireless-emulator,keysight:dtx/solutions/facets/industry/6g
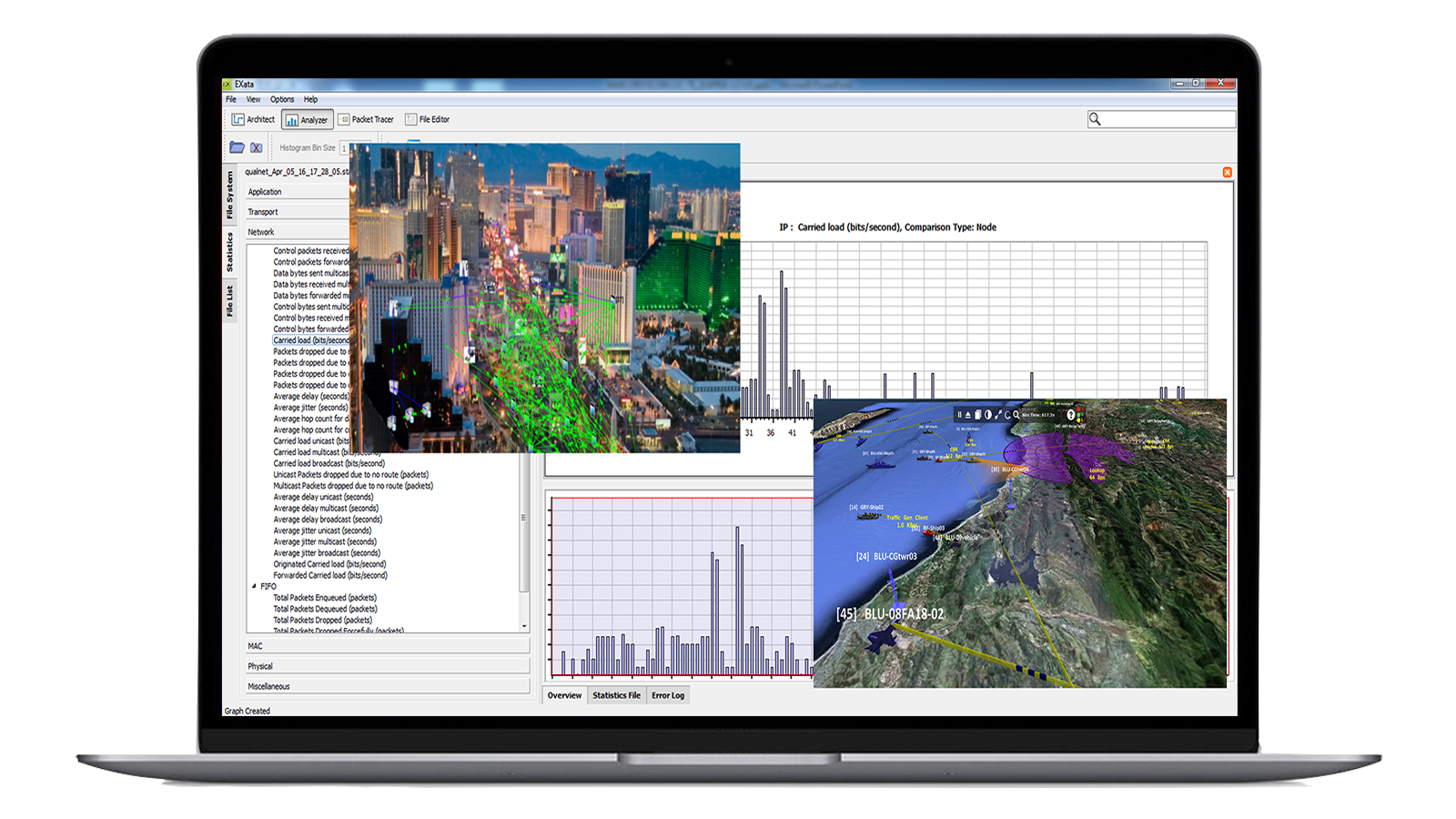
How to Emulate Non-Terrestrial Networks in the Lab
NTN test requires laboratory reconstruction of all possible NTN scenario permutations. Learn how to perform end-to-end testing and validation of NTN deployments.
Learn more